
[Task 1]
This section goes over a quick explanation of nmap in the world of pentesting.
ANS 1: There is nothing needed to be done. Press complete and away we go!
[Task 2] Nmap Quiz
A short quiz on the more useful switches that we can use with Nmap.
Question 1: First, how do you access the help menu?
Mostly help flag is represented by -h.
ANS 1: -h
Question 2:Often referred to as a stealth scan, what is the first switch listed for a ‘Syn Scan’?

ANS 2: -sS
Question 3: Not quite as useful but how about a ‘UDP Scan’?

ANS 3: -sU
Question 4: What about operating system detection?
With the help of hints we can analyse it’s a one word flag.

ANS 4: -O
Question 5: How about service version detection?

ANS 5: -sV
Question 6: Most people like to see some output to know that their scan is actually doing things, what is the verbosity flag?

ANS 6: -v
Question 7: What about ‘very verbose’? (A personal favorite)
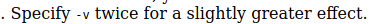
ANS 7: -vv
Question 8: Sometimes saving output in a common document format can be really handy for reporting, how do we save output in xml format?
XML, the extensible markup language, has its share of critics as well as plenty of zealous proponents.
ANS 8: -oX
Question 9: Aggressive scans can be nice when other scans just aren’t getting the output that you want and you really don’t care how ‘loud’ you are, what is the switch for enabling this?
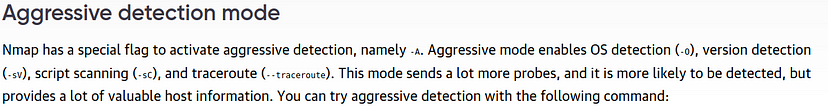
ANS 9: -A
Question 10: How do I set the timing to the max level, sometimes called ‘Insane’?
-T paranoid|sneaky|polite|normal|aggressive|insane
While the fine-grained timing controls discussed in the previous section are powerful and effective, some people find them confusing. Moreover, choosing the appropriate values can sometimes take more time than the scan you are trying to optimize.

ANS 10: -T5
Question 11: What about if I want to scan a specific port?
**Scan a single Port** :** **nmap -p 22 192.168.1.1
ANS 11: -p
Question 12: How about if I want to scan every port?
**Scan all 65535 ports : ** nmap -p- 192.168.1.1
ANS 12: -p-
Question 13: What if I want to enable using a script from the nmap scripting engine? For this, just include the first part of the switch without the specification of what script to run.
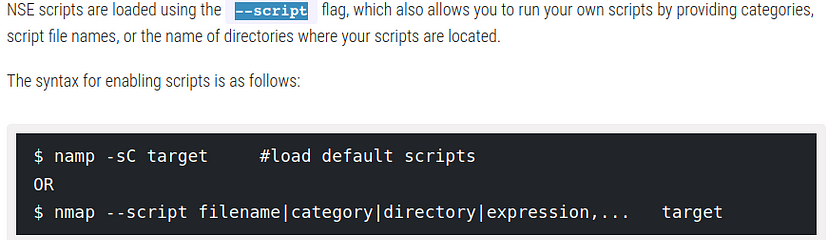
ANS 13: –script
Question 14: What if I want to run all scripts out of the vulnerability category?
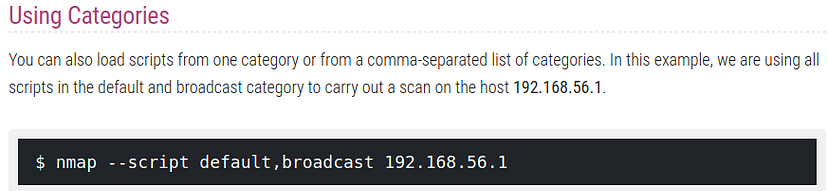
ANS 14:–script-vuln
Question 15: What switch should I include if I don’t want to ping the host?

ANS 15: -Pn
[Task 3] Nmap Scanning
Question 1: Let’s go ahead and start with the basics and perform a syn scan on the box provided. What will this command be without the host IP address?
ANS 1: nmap -sS
Question 2: After scanning this, how many ports do we find open under 1000?
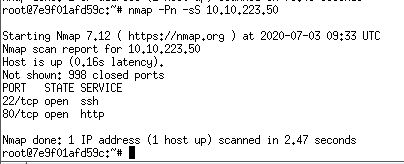
ANS 2: 2
Question 3: What communication protocol is given for these ports following the port number?
From the above screenshot, tcp protocol is given
ANS 3: tcp
Question 4: Perform a service version detection scan, what is the version of the software running on port 22?
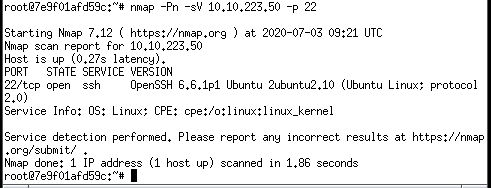
ANS 4: 6.6.1p1
Question 5: Perform an aggressive scan, what flag isn’t set under the results for port 80?
ANS 5: httponly
Question 6: Perform a script scan of vulnerabilities associated with this box, what denial of service (DOS) attack is this box susceptible to?
Tests a web server for vulnerability to the Slowloris DoS attack without actually launching a DoS attack.
This script opens two connections to the server, each without the final CRLF. After 10 seconds, second connection sends additional header. Both connections then wait for server timeout. If second connection gets a timeout 10 or more seconds after the first one, we can conclude that sending additional header prolonged its timeout and that the server is vulnerable to slowloris DoS attack.
ANS 6: http-slowloris-check
RESOURCES:
Nmap: the Network Mapper — Free Security Scanner How to Use Nmap Script Engine (NSE) Scripts in Linux
Completed this one.. See ya
:wq